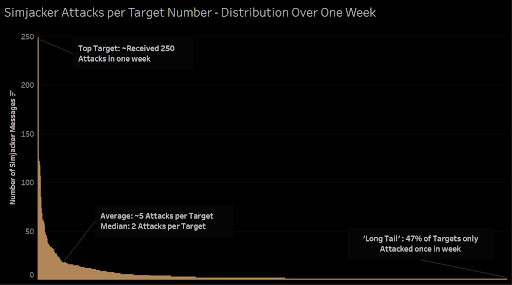
A new Stuxnet-level vulnerability named Simjacker used to secretly spy over mobile phones in multiple countries for over 2 years: Adaptive Mobile Security reports | Packt Hub
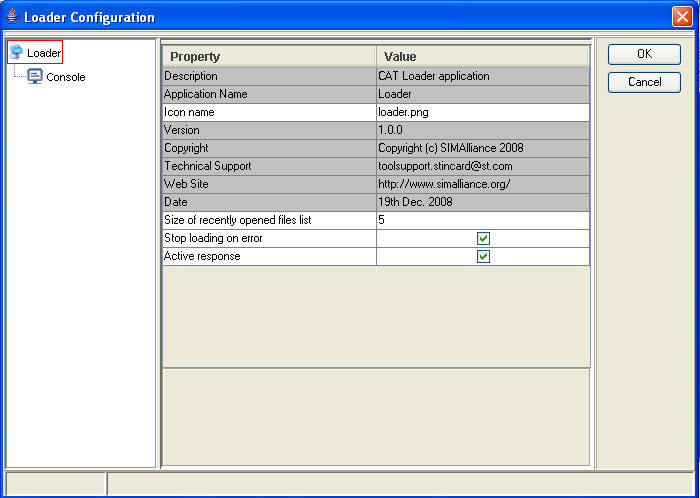
SIMAlliance Interoperable Loader Download - It allows network operators and developers to manage ETSI toolkit applications
SIMAlliance Interoperable Loader Download - It allows network operators and developers to manage ETSI toolkit applications